Project description
The rationale behind BIECO’s concept is to deliver a framework for improving trust and security within ICT supply chains. These are complex ecosystems comprising several heterogeneous technologies, processes, actors (e.g., end-users, software or hardware providers and organizations) and resources, all of which generate or exchange data forming extremely complex information management systems.

BIECO holistic approach
BIECO will offer a holistic approach for building and validating several technologies and methodologies that are specifically oriented to foster security and trust within ICT ecosystems.
The goal is to instantiate the framework iteratively in order to enable a continuous assessment and improvement of ICT supply chain’s security, given the speed at which the cybersecurity landscape evolves with new threats emerging every day.
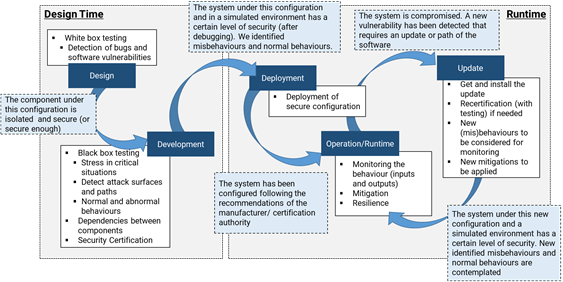
To better illustrate how BIECO intends to address these challenges along the entire lifecycle of the ICT supply chain, the above figure shows broadly the interaction flow between the different phases of the lifecycle, as well as the core functionalities involved.
To realize this vision, BIECO’s architecture will thus contain a set of interoperable tools and methodologies capable of ultimately ensuring the trustworthy execution of systems and system components within complex digital ecosystems. From design to runtime, vulnerabilities and failures are detected, evaluated and mitigated together with prompt reactions that ensure the ultimate trustworthy execution of systems and system components. In order to open the path towards future development and for enabling the possibility to keep up to agile technological progress supported by runtime updates of systems (including safety-critical systems), we further on design the BIECO architecture with expandability in mind. One possibility in this direction will be that based on detected deviations, runtime updates of systems can be accommodated through a natural extension of the BIECO framework, including the feedback of information to the design time for continuous improvement..
Components of the BIECO Framework
Vulnerability assessment
This asset will focus on improving the detection of vulnerabilities within ICT components.
This asset will focus on improving the detection of vulnerabilities within ICT components and understanding how a certain vulnerability can propagate across the whole supply chain and impact other systems that are not subject to the same vulnerability. In order to do this, an advanced machine learning-based tool for vulnerability detection will be developed, putting a special focus on improving aspects such as the accuracy or usability of the tool. Regarding the propagation of vulnerabilities, methodologies such as ant colony optimization, and other vulnerability propagation analysis techniques will be explored.

Resilience mechanisms
As some vulnerabilities might remain undetected, it is necessary to adopt a preventive approach and assume that a cyberattack will happen, exploiting that vulnerability.
In the ICT supply chain this is a serious issue, as it can put at risk not only the vulnerable system but also the complete supply chain. Therefore, BIECO will explore new methods to guarantee the resilience of the systems, ensuring recovery in case an attack occurred. This will be done by performing self-checks on the systems, forecasting the failures of the different components and their impact on the supply chain and offering methods to bring systems into a safe-operation state.
Auditing processes
Understanding the security guarantees provided by each of the ICT components, as well as their interactions with other elements of the supply chain, is crucial in order to ensure the integrity of the whole ecosystem.
For that purpose, simulation models that represent accurately the behaviour of ICT systems and components within a supply chain will be generated. Unknown interactions between components, the integration of new systems within the supply chain, or changes environmental and operational conditions will also be monitored, and behavioural profiles (MUD) will be generated to monitor suspicious behaviours that could represent a possible attack to the system.

Risk analysis
BIECO will provide a tool audit complex algorithms and interconnected ICT systems.
BIECO will provide a tool audit complex algorithms and interconnected ICT systems, including the analysis of the interaction between components when they are exploited. The tool will also offer a visual representation of the possible attack paths, as well as support to safety aspects, analyzing the impact of vulnerabilities in a cyber-physical system that could derive into a physical hazard.
The BIECO Design Phase Architecture
The architecture for the design phase is provided in figure below. It encompasses the application layer, where BIECO’s main services are included, the data management layer for persistence of historical data, the integration middleware and the controlled environment being assessed.
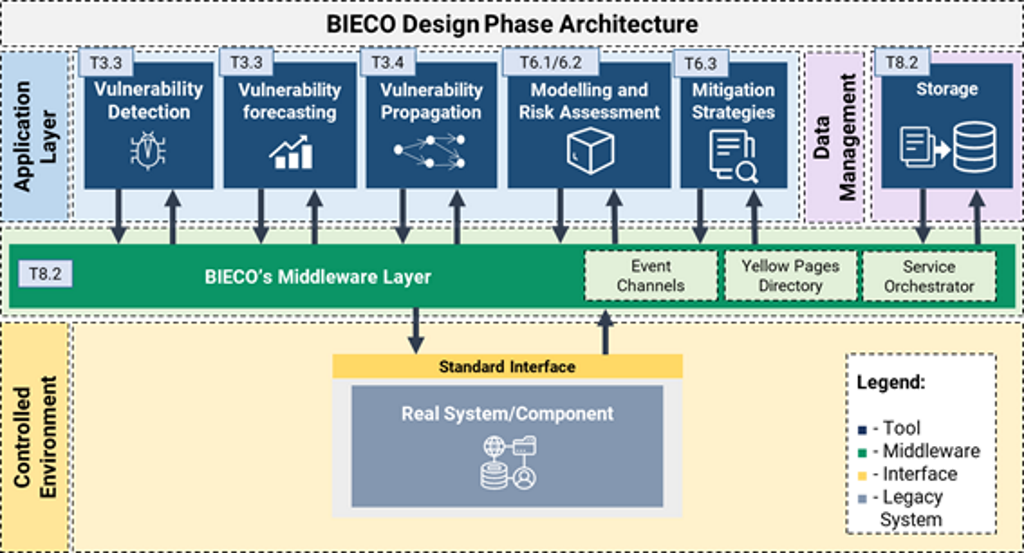
BIECO’s Design Phase Architecture
BIECO project will address the validation of the product security adapting well known standards and approaches such as ARMOUR project, ETSI EG 203 25 or ISO 27001, to the needs identified within the software supply chain.
In particular, BIECO will consider the following processes:
Context establishment:
As a starting point, BIECO will consider the best practices, regulation, recommendations and existing vulnerabilities to create a security profile against which the product should be validated.
Vulnerability assessment:
Taking into account the existing vulnerabilities from the context establishment, it will aim at identifying known vulnerabilities in the source code, and analysing their possible impact in the own software or other related modules.
Modelling:
It serves to model the system, its complex structure and interfaces, with the aim of identifying since the early prototyping stage, which are the weakest components, and of representing the paths and possible interactions when attacks are exploited.
Treatment:
As a result of the evaluation, and dealing with the security problems encountered, BIECO will generate a behavioural profile. This profile will contain a set of security policies that the product should follow to guarantee a secure functioning.
Security testing:
The security evaluation is meant to be objective, based on empirical data coming from testing. In this sense, the previous steps of context establishment and vulnerability assessment will guide the definition of the tests. For automation purposes, BIECO will follow a Model Based Testing (MBT) approach from the modelling phase, in which the system and tests are designed at a high level and simulated to verify the compliance of the system with respect to the profile.
Security risk assessment:
The outputs of the modelling and testing processes will be used to measure the overall security level of the product.
Labelling:
The results of the evaluation will be communicated in a visual and simple way to non-expert consumers, so it can be used to compare the security of similar products.
The BIECO Runtime Phase Architecture
The runtime phase refers to the stage after launch/deployment of a product which has been previously validated and certified. Within the context of BIECO its purpose is to ensure that the product remains secure and within its expected functional boundaries during usage by leveraging the different runtime tools developed in WPs 3-6, deployed within BIECO’s digital platform implemented within WP8. An overview of BIECO’s runtime architecture can be seen below.

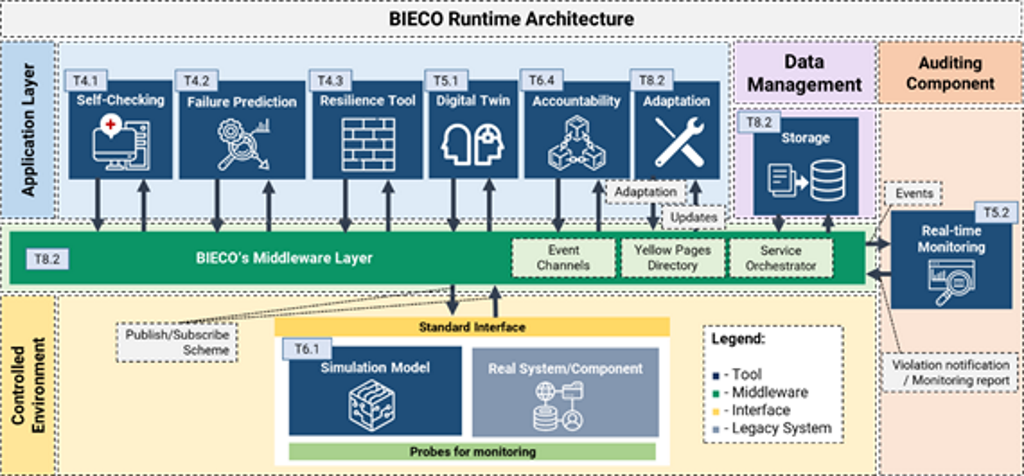
Resilience mechanisms
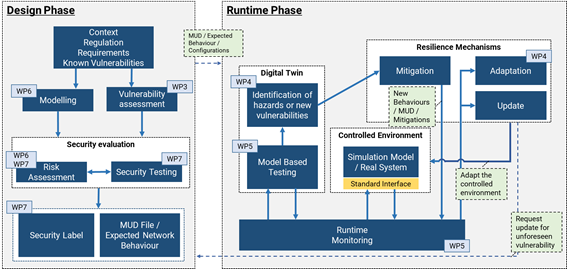
During the design phase, the software is designed, the functional and security requirements are analyzed, the software is implemented, tested, and it can even be certified.
All this valuable information is lost when the product is released into the market if we do not establish a link between the design phase and the execution phase. In this sense, BIECO establishes this link through not only the security certificate (label) that is generated as a result of the security evaluation, but also through a behavioral profile.
All this valuable information is lost when the product is released into the market if we do not establish a link between the design phase and the execution phase. In this sense, BIECO establishes this link through not only the security certificate (label) that is generated as a result of the security evaluation, but also through a behavioral profile.
Manufacturer Usage Description (MUD)
BIECO will base the definition of the behavioral profile on the recently standardized Manufacturer Usage Description (MUD). The MUD uses high-level terms that allow defining several behaviors in a compact way.

This way, the MUD abstracts from all the information that depends on the domain in which the device will be installed, such as IP addresses. However, the expressiveness of the MUD model is limited to certain network aspects (ports, Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) and network access control), and therefore, more fine-grained security aspects or related to other protocol stack’s layers cannot be described. BIECO will extend the MUD model to allow the definition of additional behaviors beyond firewall-like behaviors, providing extra relevant information from the design phase to the runtime.
The extended MUD profile will be generated from the security evaluation process that takes part during the design phase, combining the information coming from the original MUD file with the results of the testing and the risk assessment processes . As a result, the extended MUD file will be published in the manufacturer’s server, so it can be requested during the runtime.
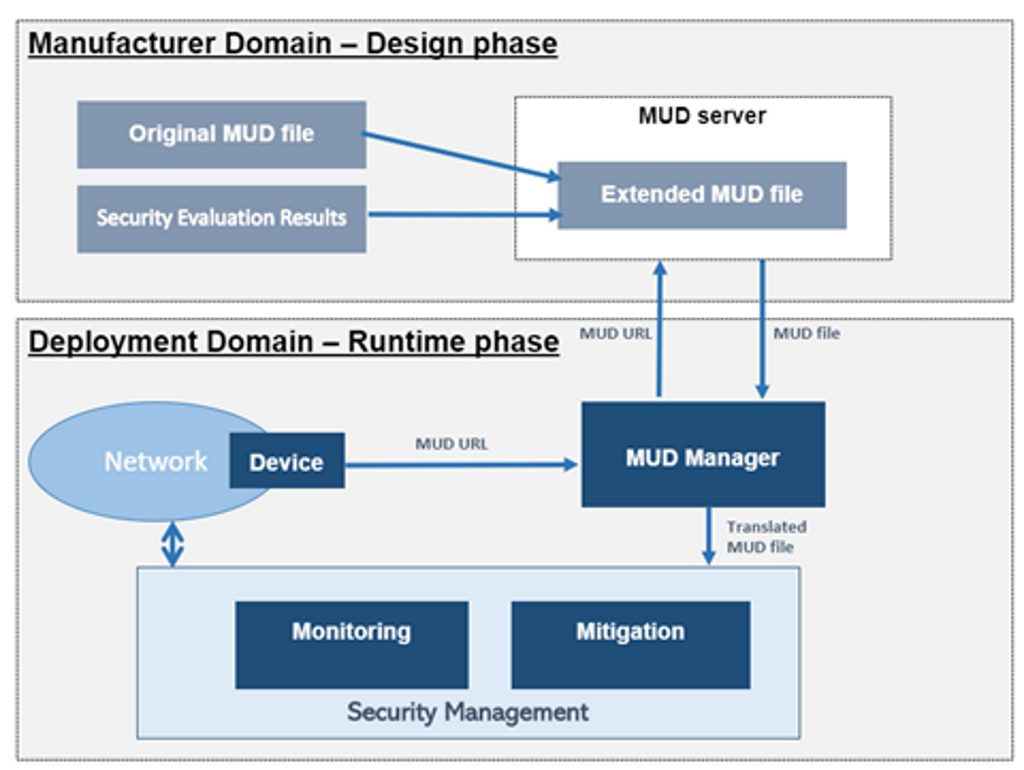
A possible future extension of this behavior (beyond the initial scope of BIECO) would be to link back to the design phase, enabling the system to autonomously request an update to deal with the unforeseen hazard or vulnerability .
Finally, if the applied mitigation is inconsistent with the MUD specifications, it will mean that the behavioral profile will need to be adapted, which can lead to a possible update of the MUD by the manufacturer, closing the interaction cycle between the design phase and runtime phase.

