- Introduction
With progressing digitalization and the trend towards autonomous computing, systems tend to form digital ecosystems, where each participant (system or actor) implements its own operational goals. Systems operating within ecosystems can deploy smart agents in the form of software applications, which would enable cooperative behaviour with other ecosystem participants and achievement of common tactical and strategic goals. Effective collaboration within these emerging digital ecosystems strongly relies on the assumption that all components of the ecosystem operate as expected, and a level of trust among them is established based on that. In BIECO we design mechanisms that ensure the collaboration between ecosystem participants remains trustworthy in case of failures. By making systems resilient in face of malicious attacks, a trustworthy behaviour is always displayed to the user (which can be an interacting service or a human user).
The key difference between digital ecosystems and systems of systems is that digital ecosystems involve actors with goals, which significantly influences the dynamics within an ecosystem. In cooperation, the actors might have not only collaborative goals, but also competitive goals, which may influence the health of the ecosystem. In digital ecosystems, where hardware and software components of cyber-physical systems are provided by different actors, malicious behaviour can be introduced along with software components by actors who join a smart ecosystem based on declared collaborative goals, but who are actually acting in competition.
Typically, the admission to a digital ecosystem has been based on the actors’ commitment to published roadmaps organized and provided by an ecosystem orchestrator for the long term. Emerging digital ecosystems, however, are particularly faced with the challenge of intended malicious behaviour which may be hidden in the smart agents. As a consequence, besides being functionally correct, a trusted digital ecosystem also needs to assess the participants’ trustworthiness before granting them admission. Assessing the trustworthiness of ecosystem participants requires new platforms that enable behaviour evaluation at runtime, with this being one of the main goals of BIECO.
Thus, this deliverable aims to provide the initial set of guidelines and specifications concerning the design and implementation of the BIECO solution for improving the resilience and trustworthiness of digital ecosystems, building on the requirements derived in D2.1 and the ongoing work of T2.2 concerning the use case specification. These will be provided as the first draft of the BIECO overall framework architecture, which will be later revised, completed and finalized in D2.4, due in M18.
The remainder of this document is structured as follows: Section 2 presents a recap of the BIECO concept, serving as the conceptual context for this deliverable. Following this, each of the framework’s components (organized by WP) is detailed in Section 3, including an initial description of their role and internal architecture, along with its main interactions and planned interfaces. This acts as the foundation for the first draft of the BIECO architecture, which is presented in Section 4. This specification encompasses different phases of the ICT lifecycle, from design to runtime, with each being depicted in its own view. Finally, Section 5 concludes the document with a brief summary of the main outcomes and future outlook.
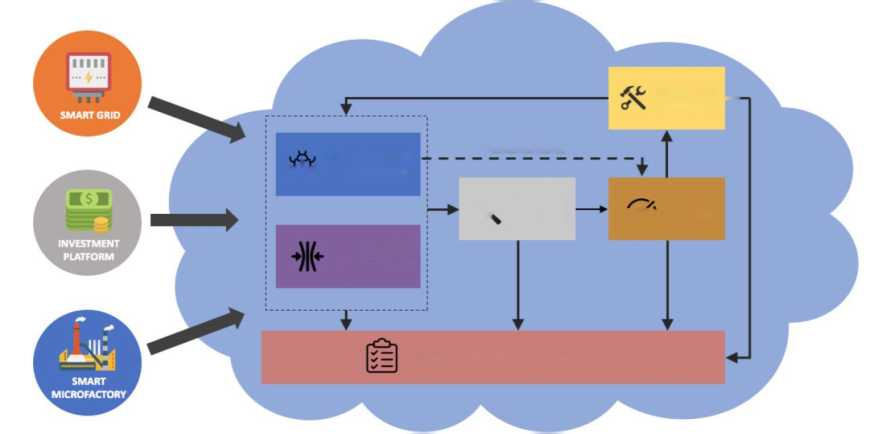
The rationale behind BIECO’s concept is to deliver a framework for improving trust and security within ICT supply chains. These are complex ecosystems comprising several heterogeneous technologies, processes, actors (e.g., end-users, software or hardware providers and organizations) and resources, all of which generate or exchange data forming extremely complex information management systems.
Due to this, cybersecurity and integrity are particularly important aspects to take into account in this context, which need to be addressed with an integrative approach that contemplates the entire chain, as opposed to restraining it only to the individual components.
In this direction, BIECO aims to deliver a holistic approach to building and validating methodologies and technologies tailored to foster security and trust within ICT ecosystems.
The goal is to instantiate the framework iteratively in order to enable a continuous assessment and improvement of ICT supply chain’s security, given the speed at which the cybersecurity landscape evolves with new threats emerging every day. As shown, the methodologies and tools developed or adapted in this context will be evaluated in three use cases from different sectors, namely smart grid / energy, financial and manufacturing industry sectors. To better illustrate how BIECO intends to address these challenges along the entire lifecycle of the ICT supply chain, Figure 2 shows broadly the interaction flow between the different phases of the lifecycle, as well as the core functionalities involved.
To realize this vision, BIECO’s architecture will thus contain a set of interoperable tools and methodologies capable of ultimately ensuring the trustworthy execution of systems and system components within complex digital ecosystems. From design to runtime, vulnerabilities and failures are detected, evaluated, and mitigated together with prompt reactions that ensure the ultimate trustworthy execution of systems and system components. In order to open the path towards future development and for enabling the possibility to keep up to agile technological progress supported by runtime updates of systems (including safety-critical systems), we further on design the BIECO architecture with expandability in mind. One possibility in this direction will be that based on detected deviations, runtime updates of systems can be accommodated through a natural extension of the BIECO framework, including the feedback of information to the design time for continuous improvement.
3. Components of the BIECO Framework
This section details each of the core functionalities contemplated in the BIECO framework, along with their respective tools divided by each of the WPs. The main purpose is to provide a foundation for the specification of the architecture and later on serve as a reference point for the development efforts within each WP.
3.1. Vulnerability Management (WP3)
Vulnerability assessment is an essential step of security management that allows to detect and analyse on an early stage the possible security flaws or bugs of a system. Even though the vulnerabilities can be addressed at any stage of a system lifecycle, their early identification helps to reduce the risks in general, minimizing the costs as well as the probability of a later exploitation by an attacker. In general terms, vulnerabilities can be associated to software, hardware, policies or even to the behaviour of users (intended or unintended). In particular, in BIECO the vulnerability assessment process is focused on the identification of vulnerabilities that appear in the source code during the design time of a software, and that could end having an impact on the confidentiality, integrity or availability of the system. This vulnerability assessment is not only focused on the detection of software vulnerabilities, but it aims also at analysing the possible long-term impact that the identified vulnerabilities could have, taking into consideration aspects such as the period of time under which they might be exploited, or how they could propagate to other components of the software supply chain. It is important to highlight that the vulnerability assessment performed in WP3 is focused only on design time, taking into account a static view of the source code, and it does not analyse other aspects associated to the execution or behaviour of the software during runtime, which are considered within other BIECO work packages (WP4, WP5, WP6).
3.1.1. General Description
The tools of WP3 will be developed mainly as REST services and deployed as part of the BIECO platform. These tools will rely mainly on the use of Machine Learning techniques and their purpose is to support different aspects of the assessment process of a software vulnerability, including its identification in a piece of source code, the evolution of its exploitability over time and its possible impact on other parts of the software (or even other systems that integrate the software under analysis, as part of a supply chain).
The tools that will be developed in the work package are:
• Data collection and pre-processing: REST service that collects data directly from BIECO pilots and from public data sources. The resulting datasets are delivered to the internal stakeholders using a REST API. The specifications and examples are delivered using the Postman application.
• Vulnerability detection: a tool that enables the identification of software vulnerabilities in source code. The tool, based on Machine Learning and data mining techniques, considers the use of privacy preserving techniques such as Federated Learning, in order to improve its accuracy and ensure confidentiality for the non-public training datasets (e.g., the source code from use cases).
• Forecasting: it will follow two different approaches.
o Exploitability forecasting: the tool allows, taking as an input a vulnerability detected in a certain piece of source code, to predict the time frame in which the vulnerability could be exploited.
o Vulnerability forecasting: RESTful web service that, based on the dataset delivered by the API developed in T3.2, allows to forecast the number of vulnerabilities that will appear in a time frame.
• Vulnerability propagation: tool developed also as a REST service that provides a visual representation on how a certain vulnerability can propagate across the source code of one or more software modules. The tool provides a graph-based representation, as an intuitive manner of visualizing the different propagation paths of the vulnerabilities.
As far as possible, the tools will be deployed by means of containers technologies such as Docker[1]. This technology allows easily to create, test, deploy and scale applications. The containers include all the libraries and dependencies that the tools require in order to be executed, and they avoid issues with specific dependencies of the versions of operating systems.
3.1.2. Actors
The actors of WP3 tools will be in principle software developers/owners (e.g., the use cases providers) who are interested in determining if their source code contains any vulnerabilities and, in case they exist, understand to which extent they could have an impact on their systems, and even business processes. In order to ease the interaction with the tools, a GUI (Graphic User Interface) will be provided to the actors.
3.1.3. Interactions
The Figure 3 presents the interactions of the tools provided by WP3 with the rest of tasks and work packages in BIECO.
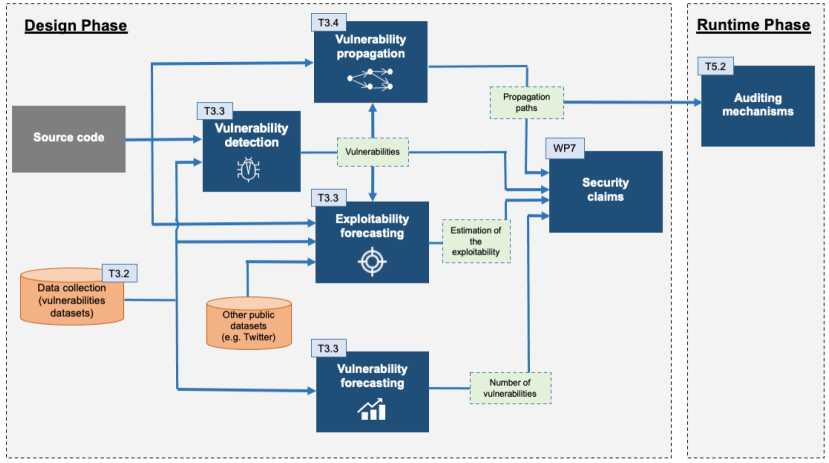
The vulnerability assessment process can begin through the instantiation of two alternative components: i) the vulnerability forecasting tool from T3.3 that allows to forecast the number of vulnerabilities that will appear in a certain period of time, taking into account just information from vulnerability datasets; or ii) the vulnerability detection tool developed also in T3.3, which takes as an input the source code to analyse and public information from the vulnerabilities (such as its type or the CVE). The vulnerabilities detected in this step can be further assessed by means of two additional tools developed within the work package: the exploitability forecasting tool from T3.3 that allows to determine in which period of time the detected vulnerability might be exploited, and the vulnerability propagation tool from T3.4 that allows to model how the detected vulnerability can impact other dependant software modules.
It is important to note that since WP3 requires source code as an input, privacy preserving mechanisms will be explored to protect sensitive data and intellectual
property. This could include the use of federated learning, differential privacy, or secure multi-party computation schemes.

