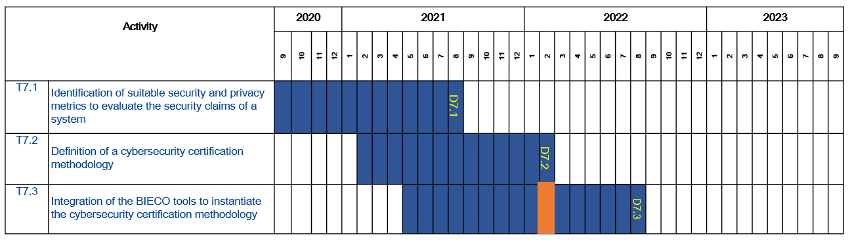
WP7 has closed its second task, finishing the security evaluation methodology that is intended to be instantiated in the last task of the WP. Currently, we are working very hard on the demo for the project intermediate review in which we will show pieces of the methodology over the use case proposed by the project leader UNINOVA.
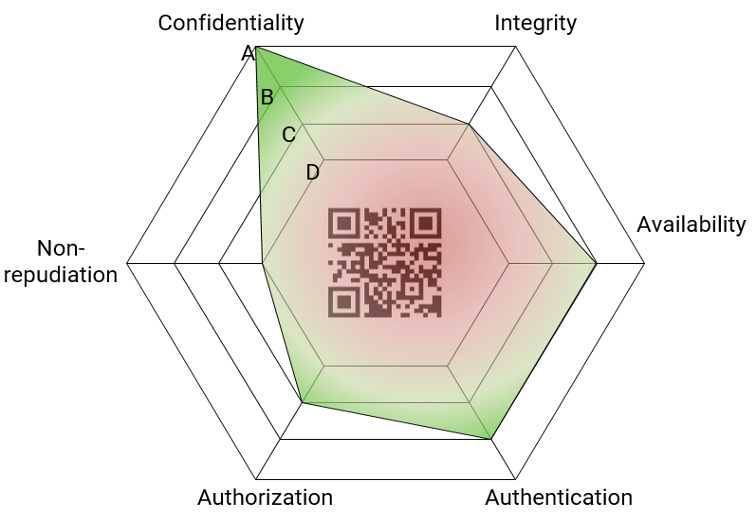
On the 16th of February took place the WP7 monthly meeting. We have just finished D7.2 and its corresponding T7.2, providing the final version of the security evaluation methodology developed within BIECO. The deliverable presents an overview of the state of the art in certification, risk assessment and testing, analysing the challenges that are associated with the evaluation process. Taking into account this, the methodology is composed of a series of steps which address the integration of the context variable, an objective and empirical evaluation, dependencies between components, a visual label and a treatment process based on the MUD standard.
Currently, all the partners of the project are focused on the demo for the project intermediate review. In WP7 we will show pieces of the methodology applied to the use case proposed by UNINOVA. We selected 3 different security claims from T7.1 that leads to 6 tests and we are modelling and defining the tests with GraphWalker and the fuzzing tool from GRADIANT to validate that the claims are fulfilled by the system of the use case. Furthermore, the tool from 7bulls will integrate the test results to generate the security label. We are also coordinating with HOLISUN, which is in charge of the BIECO orchestration to integrate all the tools and design the GUI.